How to Tell If Someone Is Accessing Your iPhone Remotely [Solved]
Your iPhone holds more than just apps; it holds your life. So when it starts acting up, it is natural to wonder if someone else is behind it. Perhaps you run out of battery so fast, and your settings are modified automatically, or you find certain uninstalled apps that are still installed. These may be hidden hints. The world of easier-than-ever remote access necessitates being on guard. In this guideline, you will learn how to detect the signs and act. Here is how to tell if someone is accessing your iPhone remotely, plus simple ways to protect your device before things get out of hand.

In this article:
Part 1. How Can I Tell if Someone is Approaching My iPhone Remotely?
If your iPhone has been feeling off lately, it might not just be a glitch; it could be a sign that someone else is poking around where they should not be. Asking someone can access my iPhone from another device is more common than you think, and the answer is yes, if the right precautions are not in place.
1. Unusual Battery Drain
If your battery suddenly starts draining in just a few hours, even when you are not using the phone heavily, it could be a sign that a hidden app or tool is running in the background without your permission.
2. Overheating for No Clear Reason
Your iPhone heating up while idle or during light use is not normal. This could mean that an unauthorized people tracking your device is working behind the scenes, such as a third-party app or a hidden management profile.
3. Unexpected Data Usage Spikes
A sudden increase in your data usage might mean your iPhone is sending or receiving information without you knowing. Remote access apps often operate quietly and can eat up data even when the screen is off.
4. Strange or Unknown Apps Appear
If you find apps you do not remember downloading, that is a red flag. Someone could have installed a malicious app remotely, especially if your phone has an MDM profile or has been jailbroken in the past.
5. Privacy Dots Without Any App in Use
The orange or green dots on your screen show when your microphone or camera is being used. If these appear and you have not opened any relevant apps, it could mean someone is remotely accessing those features without your knowledge.
Part 2. Remove Unknown MDM Profile to Block Remote Access to iPhone
Method 1: Use iMyPass iPhone Unlocker (No Password Needed)
In case you do not have the admin password or the access credentials, then a dependable alternative is to use imyPass iPassGo. This is a tool that can be used to eliminate the MDM profiles without any system login details. It can work even with a supervised or constrained iPhone by a third-party administrator. By unlocking your device through a couple of simple clicks, you will be able to remain fully in control of its features. If you are wondering how to stop someone from accessing your iPhone remotely, iPassGo offers a fast, secure, and user-friendly solution that requires no technical skills.
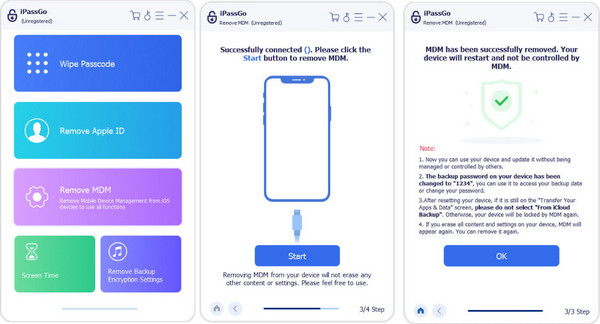
Method 2: Remove MDM Manually With Password
If an organization added the Mobile Device Management profile you are part of, such as a workplace or school, and you have the password, you can remove it directly from the iPhone. To do this, open Settings > General > VPN & Device Management or Profiles & Device Management on older iOS versions, select the profile, then tap Remove Management and enter the administrator password when prompted. Once removed, your device will no longer be managed remotely.
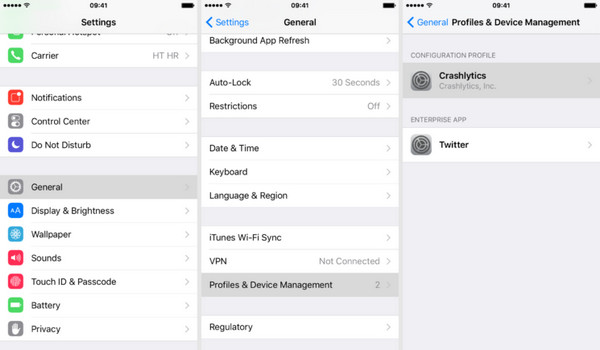
Part 3. Six Built-in Ways of iPhone to Block Remote Access
1. Remove Apps from Unknown Sources on iPhone
Begin by examining your Home Screen, your App Library, and other apps that you cannot recall having installed. Untrusted or unknown applications may have been installed with the same Apple ID or installed with an MDM profile. To remove them, press and hold the app button, tap Remove App, then confirm deletion. Also, go to Settings > General > VPN & Device Management to make sure no hidden profiles are controlling app installations.
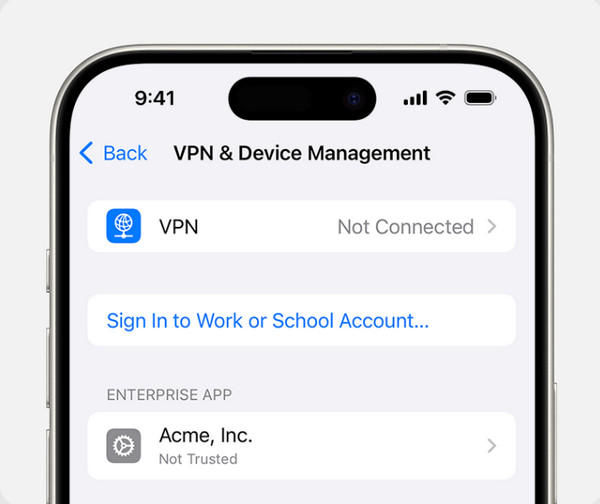
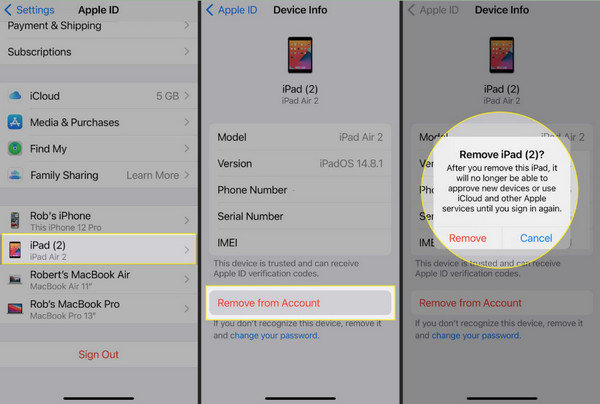
2. Remove Unfamiliar Devices from Your Apple ID
How to know if someone has access to your iPhone? Your Apple ID can be linked to multiple devices, and if one of them does not belong to you, that could be a problem. Head to Settings > your name > Devices to view all devices currently signed in to your Apple ID. Tap any unknown device, then select Remove from Account.
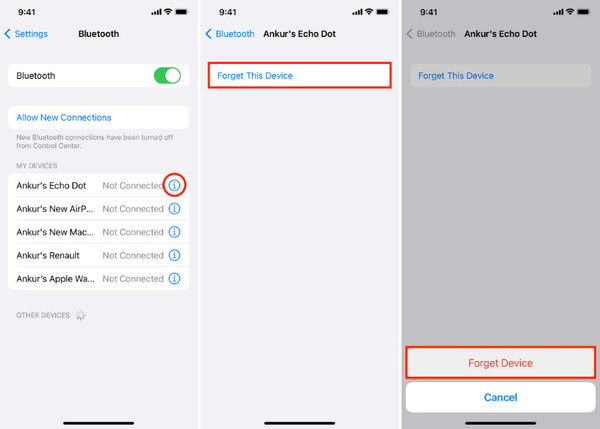
3. Disconnect and Remove Unknown Bluetooth Devices
A hidden connection through Bluetooth can sometimes be used to access your device locally. Go to Settings > Bluetooth, and check the list of connected or previously paired devices. If you see something unfamiliar, tap the info button beside it and choose Forget This Device.
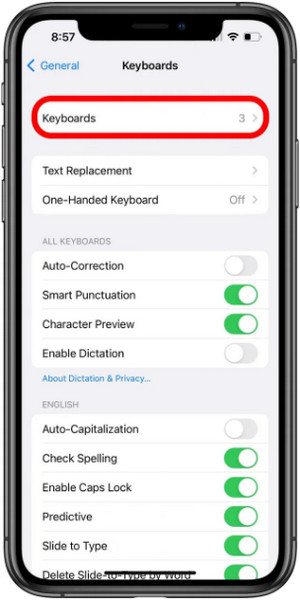
4. Remove the Unknown Keyboard
Third-party keyboards may seem harmless, but some can track what you type, even sensitive info like passwords or credit card numbers. Go to Settings > General > Keyboard > Keyboards, and review the list. If you see any keyboard you did not install or do not recognize, swipe left and tap Delete to remove it.
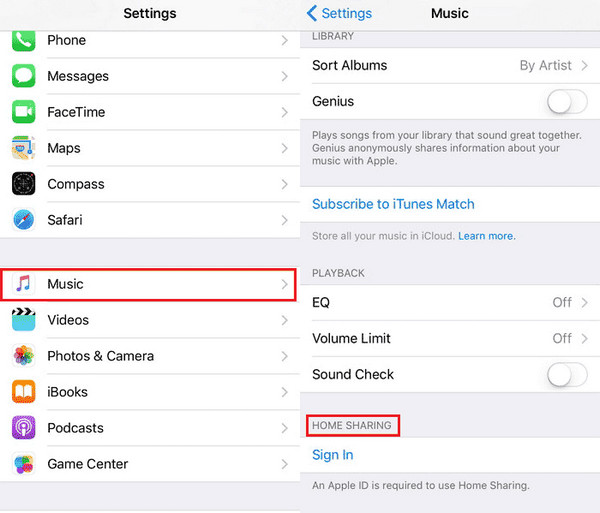
5. Remove Unknown Users from Home Sharing
Home Sharing allows other users to stream media from your library or access content from your device. If someone you do not recognize appears in your sharing list, go to Settings > Music > Home Sharing or Settings > TV > Home Sharing and review the Apple ID being used.
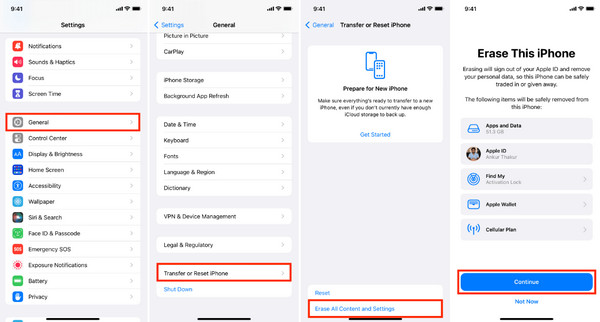
6. Restore iPhone to Factory Settings
As a last resort, restoring your iPhone to factory settings will remove all data, apps, and settings, including any hidden MDM profiles or suspicious software. Before you begin, make sure to back up your important files. Then go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings.
Part 4. How Can I Prevent Someone from Remotely Approaching My iPhone?
1. Download Apps Only from Trusted Sources
Utilize the App Store and never the third-party websites. Before downloading, it is necessary to investigate whether a well-known developer developed this application and to read user comments. Suspicious applications may contain malware that allows other people to access them remotely without your consent.
2. Avoid Clicking Suspicious Links
Never tap on random pop-ups, unknown links in texts, or spammy emails claiming your phone is infected. These are common tricks designed to trick you into installing harmful software or giving away personal information.
3. Only Allow Trusted People to Use Your iPhone
Do not hand your iPhone to strangers, even briefly. Someone with physical access could install spyware or hidden tools in seconds. Keep your device in trusted hands only, like family, close friends, or Apple staff.
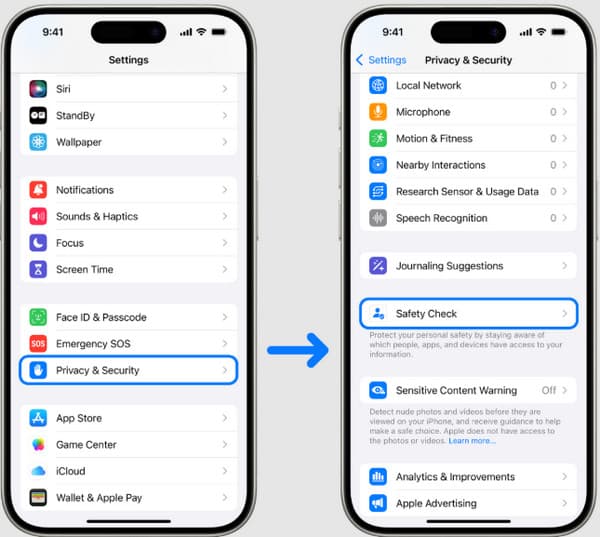
4. Check Who Can Access Your Photos, Location, and More
Go to your Privacy settings and review which contacts or apps have permission to access sensitive info. Use the Safety Check feature in Settings > Privacy & Security to quickly see and manage who has access to your data.
5. Use the App Privacy Report
Enable the App Privacy Report to monitor what data your apps and visited websites are collecting. If an app is accessing things it should not, like your microphone, camera, or location, take action by removing or limiting it.
6. Remove Malware and Reset If Needed
In case your iPhone has some indicators of malware, such as overheating, crashing applications, or rapid battery drain, begin by removing any suspicious applications. Unless that works, there is another option, which is to reset your device to erase any lurking threat.
7. Enable Lockdown Mode in Serious Cases
To get superior protection, enable Lockdown Mode. This is a drastic capability that restrains the actions of your iPhone to prevent very customized attacks. You should only use it when you feel that your device is already infected.
Conclusion
The amount of personal information available on your iPhone is rather large; thus, security must be of high priority. Although it can see what you do on your computer, these steps can allow you to take control back. If you are worried about your privacy, learning how to stop someone from accessing your iPhone remotely is the first step toward full protection. Stay alert, use the tools available, and take action as soon as something feels off.
Hot Solutions
-
Unlock iOS
- Review of the Free iCloud Unlock Services
- Bypass iCloud Activation With IMEI
- Remove Mosyle MDM from iPhone & iPad
- Remove support.apple.com/iphone/passcode
- Review of Checkra1n iCloud Bypass
- Bypass iPhone Lock Screen Passcode
- How to Jailbreak iPhone
- Unlock iPhone Without Computer
- Bypass iPhone Locked to Owner
- Factory Reset iPhone Without Apple ID Password
-
iOS Tips
-
Unlock Android
-
Windows Password

